Similar to the log analysis, I wanted to see what I could learn about my activities from a memory analysis.
So the last thing I did before I shutdown the Windows 2008 box was to take a memory dump using DumpIt.

Once I had the memory image, the first thing I did was run the "imageinfo" module on it. Obviously I did not need this as I know what the image is, but force of habit and wanting to get information like the KDBG and KPCR, etc resulted in this command being run.

Above, we gather some information about the image.
Next let's look at the network connections using the "netscan" module to see what is established. However, looking for what is listening is just as important as it can tell you if there is a backdoor waiting for connections.
Below we see there are two established connections but the one that is of greatest interest to us is the one for "powershell.exe"
I find this strange that this process has 0 threads and what looks like no handles as shown below. However, according to the Eric Pepke in this post, processes with 0 threads are zombie processes and will still have an entry in the process table. I'm ok with this explanation. Moving on!
Looking for more interesting stuff with the "pstree" module we see the following.

Above we see mimikatz has a PID of 3744. However, remember we migrated to process 2772 in this post. So the Parent of mimikatz is actually the conhost process we moved into once we gained access to the Windows server.
Additionally, as we look at the process tree we can also conclude that "esentutl" and "ntdsutil" are also children of "conhost" with PID 2772.
Let's poke around to see what we can learn from mimikatz
Using the "cmdline" module we see that mimikatz was started from "C:\x64\" folder

Let's run "cmdscan" to see what we can gather.

Looks like we got conformation that mimikatz was run from the command line.
Let's look a little deeper with the "consoles" module

From the above we learned a little bit more about the execution of mimikatz.
Looks like this was mimikatz 2.1 x64 (oe.eo).
We also see here that mimikatz was attached and uses PID 3744.
When I looked at the handles associated with PID 3744 (Mimikatz), I saw there was a handle of type process that was associated with "lsass.exe".

When I compared this to a few other processes, namely "svchost", "lsm", "ntfrs", "conhost", "vds" there was no reference for process lsass.exe. So I thought this was interesting.
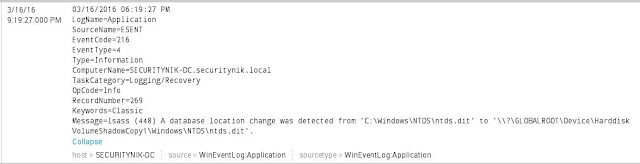
Next up I ran the "malfind" module on the lsass process which PID is 448.

From the above it seems there is injected code in the lsass.exe process.
Next up I added the "--dump-dir=/tmp" to above and then submitted the file to VirusTotal

Finally, I wanted to confirm the permission mimikatz was running with and I did this using the "getsids" module as shown below.

Ok at this point I felt this was enough for now. Virustotal did not detect this as anything malicious. This could have been for a number of reasons, some of which could have been my fault. However, I know it's not an executable. More importantly I am still working on improving my reversing skills so I left this alone for now ;-)
Hope you enjoyed this series.
Reference:
https://www.quora.com/Can-a-process-have-0-threads-or-does-one-process-always-have-one-or-more-threads-of-execution
https://github.com/volatilityfoundation/volatility/wiki/Command-Reference
https://www.aldeid.com/wiki/Volatility
Posts in this series:
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Lab Setup
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Dumping the AD database
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Mimikatz
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Exporting Certificates
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Pass The Ticket (Golden Ticket)
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Skeleton Key
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Log Analysis
Learning about Mimikatz, SkeletonKey, Dumping NTDS.dit and Kerberos with Metasploit - Volatility Memory Analysis