First step is to have a file with some sample log events of the log source you would like to test. In this case our log data looks like
----------- start of sample logs ------------
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:admin pid:27387 source: 10.0.15.20 sport:12345 destination:192.168.0.100 dport:22 protocol:tcp
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:root pid:27387 source: 10.0.15.20 sport:54321 destination:172.16.0.20 dport:22 protocol:udp
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:test pid:27387 source: 10.0.15.20 destination:10.11.12.13 protocol:icmp
----------- end of sample logs ------------
Next we will use the "logrun.pl" script in Qradar.
As always, to understand what a tool does, we should first check it's help. In this case we can get the help by executing "/opt/qradar/bin/logrun.pl" without any arguments.
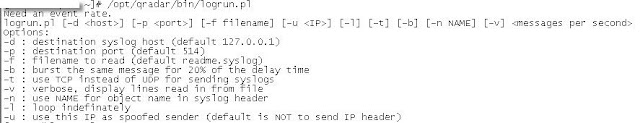
Considering the above we will use the following command:
"/opt/qradar/bin/logrun.pl -f udsm_testing.txt -t -u 10.0.0.200 10"
-f = tells the script to use filename "udsm_testing.txt". This file is our sample log
-t = tell the script to use TCP instead of UDP to send the logs
-u = tells the script to spoof the source as "10.0.0.200"
10 = tells the script to send 10 events
Let see how this works!
So did it work?! Let's find out!
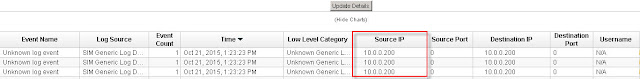
As can be seen from above "Log Activity" the logs are being seen by QRadar.
So let's try this again. Let's use a spoofed source of 172.16.0.254 and send 20 events.
Below we execute the "logrun.pl" script to generate 20 events.
And the results ...
Good stuff! Once again QRadar sees the log source. However as can be seen it does not know what to do with the logs. We will address here!
Voila. Between using this post and the one on building your first UDSM, you should be in a better position to rule the world of your QRadar SIEM.