First step is to have a file with some sample log events of the log source you would like to test. In this case our log data looks like
----------- start of sample logs ------------
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:admin pid:27387 source: 10.0.15.20 sport:12345 destination:192.168.0.100 dport:22 protocol:tcp
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:root pid:27387 source: 10.0.15.20 sport:54321 destination:172.16.0.20 dport:22 protocol:udp
Fri Mar 21 15:10:49 2014: hostname:10.0.0.1 info:Backup Started by user:test pid:27387 source: 10.0.15.20 destination:10.11.12.13 protocol:icmp
----------- end of sample logs ------------
Next we will use the "logrun.pl" script in Qradar.
As always, to understand what a tool does, we should first check it's help. In this case we can get the help by executing "/opt/qradar/bin/logrun.pl" without any arguments.
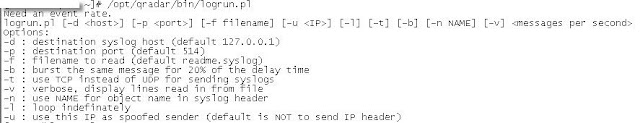
Considering the above we will use the following command:
"/opt/qradar/bin/logrun.pl -f udsm_testing.txt -t -u 10.0.0.200 10"
-f = tells the script to use filename "udsm_testing.txt". This file is our sample log
-t = tell the script to use TCP instead of UDP to send the logs
-u = tells the script to spoof the source as "10.0.0.200"
10 = tells the script to send 10 events
Let see how this works!
So did it work?! Let's find out!
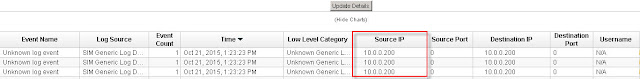
As can be seen from above "Log Activity" the logs are being seen by QRadar.
So let's try this again. Let's use a spoofed source of 172.16.0.254 and send 20 events.
Below we execute the "logrun.pl" script to generate 20 events.
And the results ...
Good stuff! Once again QRadar sees the log source. However as can be seen it does not know what to do with the logs. We will address here!
Voila. Between using this post and the one on building your first UDSM, you should be in a better position to rule the world of your QRadar SIEM.
Nice concise but informative description. Nice job!
ReplyDeleteThanks and much appreciate the comment.
DeleteThanks Nik,it works,And how to spoof source port?
ReplyDeleteHey Anonymous,
DeleteGlad you found it helpful!
Spoofing the source port is trivial. Considering the example I have above, just put whatever source port value you want for the "sport" key value pair. In my case let's say I have "sport=54321", you can then change this value to reflect whatever you want, eg "sport=12345". You can also do the same for the destination port.
Hope this helps.
thanks for reply Nik.
DeleteAlready sport added , i am using same logs as you have given above,but not succeed
What is the error you are getting? Alternatively you can email me screenshot with the issue(s)
DeleteHow about flow source?
ReplyDeleteInteresting but I never thought about the flows. Maybe I can look into it in the future.
ReplyDeleteCan you provide a sample if we want to use logrun utility for generating Qradar's internal system notifications QID logs?
ReplyDeleteFor example, if I have an event based rule which should trigger when it matches the QID (38750040). We are in a scenario where we have to do testing of Health Monitoring rules.
Please help.
I got this error following your example:
ReplyDeleteCan't call method "send" on an undefined value at /opt/qradar/lib/perl/Syslog.pm line 82, line 1.
Did I do something wrong?
Thanks!
What version are you running and are you the "root" user?
DeleteOk, the "-t" causes this problem. I removed it and then it works. Maybe the port is blocked for TCP?
DeleteHow do you spoof source port again? In your example, you put sport=12345, but your screenshot showed sourceport as 0. I got the same thing. sport in the log file does not seem to work.
Thanks.
Did you figure out exactly why this error occured? I'm having the same issue.
Delete@John Clarke
DeleteUnfortunately I never looked back at this.
It seems that none of the information from the log file is used to create the events.
ReplyDeleteYou can see from your screenshot as well.
Source IP and Destination IP are both 10.0.0.200. This comes from the "-u" value.
username is N/A.
sourceport and destinationport are both 0.
Do I need to define some kinds of template to teach QRadar to parse the log file?
Thanks.
;-) this blog is associated with the next one which we build the Universal DSM (UDSM)
DeleteLook into that blog to see how we get the events sorted out.
Could you please provide a link here?
DeleteThanks!
Here you go:
Deletehttps://www.securitynik.com/2016/04/qradar-building-your-first-universal.html
Thanks!
DeleteVery usefull ! Thank you !
ReplyDeletethanks, but where so we store the udsm_testing.txt log file?
ReplyDeleteMy suggestion is you store in anywhere. I just happen to store it in my current directory that is why I used the "-f udsm_testing.txt". If your file for example is stores in "/some/folder/path/udsm_testing.txt", then your command line should look like "-f /some/folder/path/udsm_testing.txt".
DeleteHope that helps
Yes and thanks again for the prompt response.
DeleteHello,
ReplyDeleteIs it possible to install logrun on a centOS to use it as a "replay logs server" and send logs to Qradar? I try to do this but I can't find logrun.pl anywway. Thanks for your help
Honestly, I have not looked at the code but I won't be surprised if you can just copy the file to the CentOS device.
DeleteLook at the code and see if there are any dependencies that may be needed on CentOS or any calls to other local files and or processes. If there is none you may be good to go.
I say just copy the file and see if you get any errors. If you get any you may need to work through those.
Let me know how it goes.
This comment has been removed by the author.
DeleteThanks for your reply.
DeleteI've tested it, but it doesn't seem that simple.
Indeed there seems to be a lot of dependencies and different environment variables.
I copied the /opt/qradar/lib/perl and /opt/qradar/lib/logrun.pl folders but, even if I don't get an error at the prompt and the -v option when I run the logrun.pl script lists my log file, I don't get anything on the Qradar console.
I will continue to work on this and keep you informed if there is any evolution.
Thanks to you
Log Run Dependencies
Deleteyum install perl
yum install perl-DateTime-Format-DateParse
Copy folder and content of qradar #/opt/qradar/lib/perl to VM #/opt/qradar/lib/perl
Copy /opt/qradar/bin/logrun.pl to VM# /opt/qradar/bin/
Finaly it's working fine.
ReplyDeleteThe only problem encountered is the sending of the logs in TCP which brings me back an error (I'm still looking for the cause).
So I confirm that it is possible to deport the Logrun.pl script on a remote CentOS and forward the logs to QRadar.
Glad to hear and thanks for the feedback. Much appreciated!!
DeleteHi
ReplyDeleteI am able to inject logs to Qradar.All my rules are written based on log source type.How can i assign these replay logs to its corresponding log source type automatically so that i can utilise this to test my usecases.
Thanks in Advance
thanks in advance
For it to be assigned automatically, you will need to ensure the type is one that QRadar recognizes by default.
DeleteHere's how to deport Logrun to a Redhat or CentOs machine:
ReplyDeletePrerequisites:
- Perl installed
- Date:Format.pm (Perl module) installed
Copy the Logrun.pl and Logreplay.pl scripts into the /opt/qradar/bin directory you created beforehand.
You will be able to deport your log replay this way.
I even advise to have a collector event dedicated to your log replay.
Gramy,
DeleteThanks for sticking with this and ultimately providing the guidance to your fellow readers. Much appreciated!