I recently had a request which had me pulling my hair out (it's not like I have any). The request to dump all of the QRadar rules. Having looked at the "custom_rule" table, I thought I may be able to do this. I then focused in on the "rule_data" field, only to find this information is in a manner which I could not even figure out the best way to parse.
While IBM did not have a way to do this, I was however, pointed to a location which may be helpful ... and it was very helpful. I assume, someone else may have a similar request in the future and thought I should post output here to retrieve a dump of all the rules.
The following commands will dump all rules and building blocks.
psql --username=qradar --no-align --command="SELECT rule_data FROM custom_rule" | grep "^<?xml" | sed --expression 's/<notes\/>/<notes><\/notes>/' --expression='s/.*<name>\(.*\)<\/name><notes>\(.*\)<\/notes>.*/"\1","\2"/' | sort > qradar.rules.csv
P.S. There are now a few other ways of achieving this. Check these links:
https://github.com/NdS-Research-Facilities/QRadar-ruleset
https://www.ibm.com/support/knowledgecenter/en/SSKMKU/com.ibm.qradar.doc_cloud/c_cmt_import_export_methods.html
https://www.ibm.com/developerworks/community/forums/html/topic?id=ad76e30e-0674-4be7-b376-1b34f9d24ac4&ps=25
https://developer.ibm.com/answers/questions/419663/export-list-of-rules-in-qradar/
For additional information you can visit
https://www.ibm.com/developerworks/community/forums/html/topic?id=77777777-0000-0000-0000-000014969023
Wednesday, October 7, 2015
Friday, October 2, 2015
Forensics File Carving with Bless
In this post, similar to the foremost and scalpel posts, I have a small (64 MB) flash drive with a couple of files (shown below) which were created under Windows. The assumption is someone provided me this drive as a raw image to perform a forensic investigation to retrieve whatever files are on the disk.

For this post we will carve a file using "Bless". We will pick on the pdf file at offset "1530880" and a size of "88" bytes. As to where I get this offset from, let assume one of two things. Either this offset was provided to us by someone or through a tool such as foremost or scalpel which was previously used. In this case let's use the output from the foremost post. To ensure we understand the pdf header and trailer, we will use some information from "http://www.garykessler.net/library/file_sigs.html".

So let's load up Bless and go to offset "1530880"
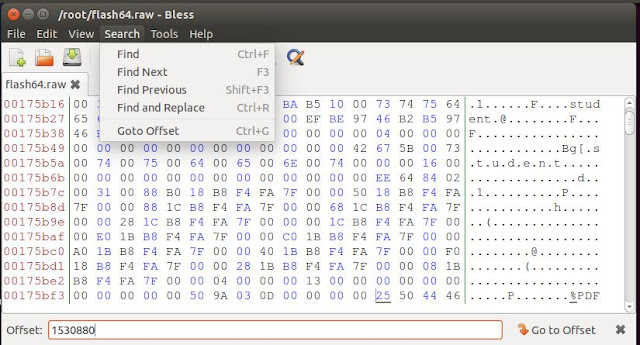
Now that we have identified at offset "1530880" there is a "pdf" header, let's now try to find the trailer. From the information provided by "http://www.garykessler.net/library/file_sigs.html" we see there are multiple possible trailers but one thing that is constant is the "%%EOF". Let's do a "find" for the first one at its absolute location.
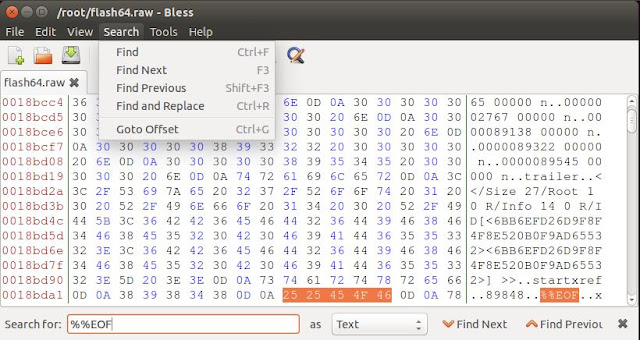
From the above, we see that "%%EOF" was found and ends at offset "1621603". Now that we have a starting offset "1530880" and an ending offset "1621603" let's try to carve our pdf file.
Lets use Bless's "Select range" menu option to obtain those bytes.
Our "Select range from" will be our starting point "1530880" and ends at "1621603".
from the image below we have highlighted all the bytes between "1530880" and "1621603"
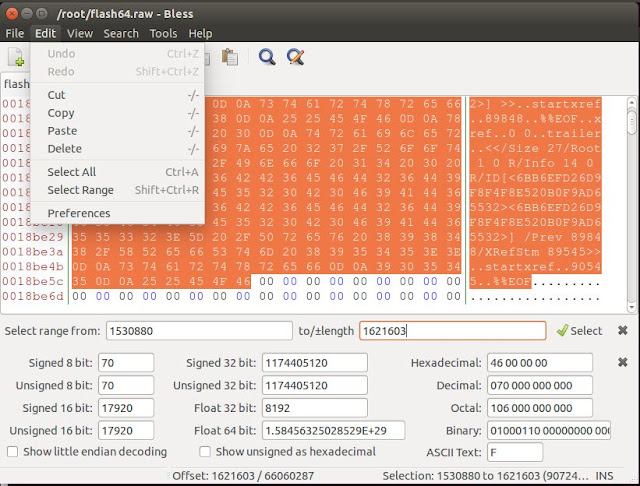
Let's now use the same menu to select "copy." Once copied, we will create a new window and paste these bytes. Next step will be to save it as "extractedPDF.pdf".
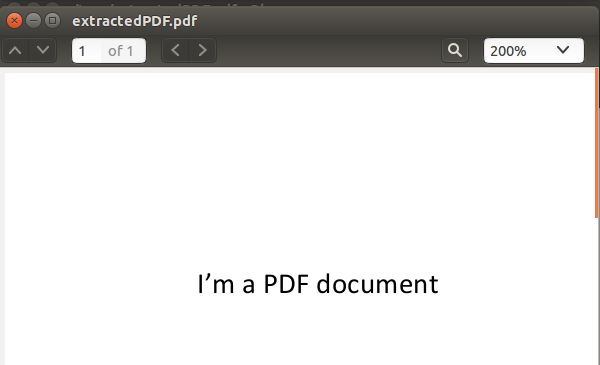
Next use your favourite pdf reader to open the file. Below we see that we have successfully carved the "pdf" file from the image.
In the posts on foremost and scalpel, tools were used to carve data. In this post the process was manual independent of tools (well except for Bless). It is important that we understand how a tool should work when we are using it to perform a task.
References:
Bless

For this post we will carve a file using "Bless". We will pick on the pdf file at offset "1530880" and a size of "88" bytes. As to where I get this offset from, let assume one of two things. Either this offset was provided to us by someone or through a tool such as foremost or scalpel which was previously used. In this case let's use the output from the foremost post. To ensure we understand the pdf header and trailer, we will use some information from "http://www.garykessler.net/library/file_sigs.html".

So let's load up Bless and go to offset "1530880"

Now that we have identified at offset "1530880" there is a "pdf" header, let's now try to find the trailer. From the information provided by "http://www.garykessler.net/library/file_sigs.html" we see there are multiple possible trailers but one thing that is constant is the "%%EOF". Let's do a "find" for the first one at its absolute location.

From the above, we see that "%%EOF" was found and ends at offset "1621603". Now that we have a starting offset "1530880" and an ending offset "1621603" let's try to carve our pdf file.
Lets use Bless's "Select range" menu option to obtain those bytes.
Our "Select range from" will be our starting point "1530880" and ends at "1621603".
from the image below we have highlighted all the bytes between "1530880" and "1621603"

Let's now use the same menu to select "copy." Once copied, we will create a new window and paste these bytes. Next step will be to save it as "extractedPDF.pdf".
Next use your favourite pdf reader to open the file. Below we see that we have successfully carved the "pdf" file from the image.

In the posts on foremost and scalpel, tools were used to carve data. In this post the process was manual independent of tools (well except for Bless). It is important that we understand how a tool should work when we are using it to perform a task.
References:
Bless
Forensics File Carving with Scalpel
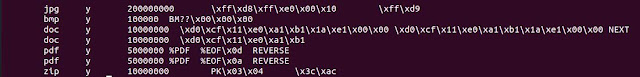
In this post, similar to the foremost post, I have a small (64 MB) flash drive with a couple of files (shown below) which were created under Windows. The assumption is someone provided me this drive as a raw image to perform a forensic investigation to retrieve whatever files are on the disk.
As with most Linux tools, before running them you may wish to see what the options are for execution by looking at the help. In this case to get help from scalpel type "scalpel -h"
Similar to the foremost post, I also modified the "scalpel.conf" file to just focus on the files which I know are on the drives.
Let's now execute scalpel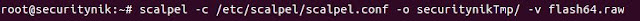
scalpel -c /etc/scalpel/scalpel.conf -o securitynikTmp/ -v flash64.raw
- c: Tells scalpel to use the configuration file which is found in "/etc/scalpel/scalpel.conf"
- o: Tells scapel to use output directory "securitynikTmp"
- v: Tells scalpel to be verbose
flash64.raw is the file which will be used as input to scalpel
Now that scalpel has executed we perform a "ls" on the "securitynikTmp" folder and see the following:

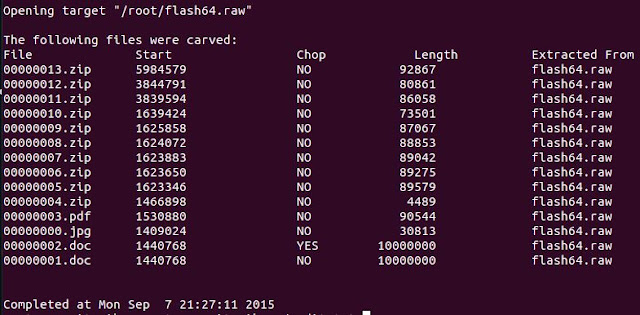
Let's look at the audit.txt to see what was extracted
root@securitynik:~# cat securitynikTmp/audit.txt
Let's look to see how well the .jpg file was extracted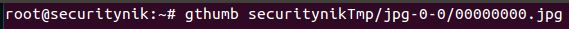
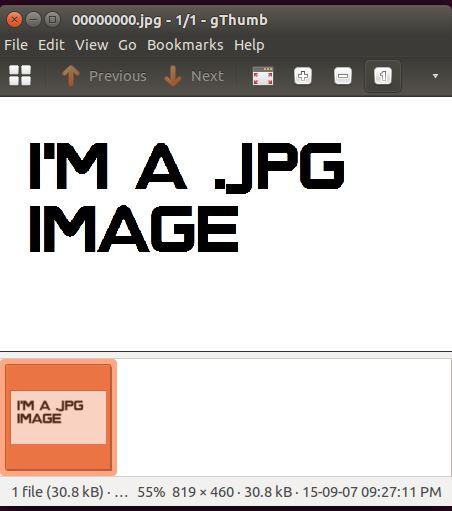
So far so good. Looks like we successfully extracted the .jpg file because we have opened and can view it with gthumb.
While tools like foremost and scalpel are helpful for automatically retrieving these files, it is also important that we understand how to do this process manually. In the next post we will leverage information learned from foremost and scalpel to manually carve a file.
References:
scalpel
gthumb
As with most Linux tools, before running them you may wish to see what the options are for execution by looking at the help. In this case to get help from scalpel type "scalpel -h"
Similar to the foremost post, I also modified the "scalpel.conf" file to just focus on the files which I know are on the drives.

Let's now execute scalpel
scalpel -c /etc/scalpel/scalpel.conf -o securitynikTmp/ -v flash64.raw
- c: Tells scalpel to use the configuration file which is found in "/etc/scalpel/scalpel.conf"
- o: Tells scapel to use output directory "securitynikTmp"
- v: Tells scalpel to be verbose
flash64.raw is the file which will be used as input to scalpel
Now that scalpel has executed we perform a "ls" on the "securitynikTmp" folder and see the following:

Let's look at the audit.txt to see what was extracted
root@securitynik:~# cat securitynikTmp/audit.txt

Let's look to see how well the .jpg file was extracted


So far so good. Looks like we successfully extracted the .jpg file because we have opened and can view it with gthumb.
While tools like foremost and scalpel are helpful for automatically retrieving these files, it is also important that we understand how to do this process manually. In the next post we will leverage information learned from foremost and scalpel to manually carve a file.
References:
scalpel
gthumb
Forensics File Carving with Foremost and dcfldd
In this post I have a small (64 MB) flash drive with a couple of files (shown below) which were created under Windows. The assumption is someone provided me this drive as a raw image to perform a forensic investigation to retrieve whatever files are on the disk.
Prior to providing an image of the drive "dcfldd" was used to create a forensic copy of the drive as shown below.
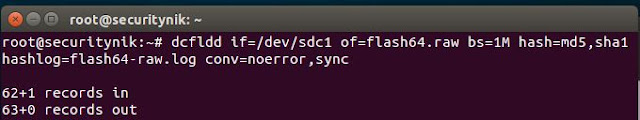
Next we verify that both the output file and the log files are created and below we see they are.
 Now let's use foremost to see if we can retrieve the same data as shown above.
Now let's use foremost to see if we can retrieve the same data as shown above.
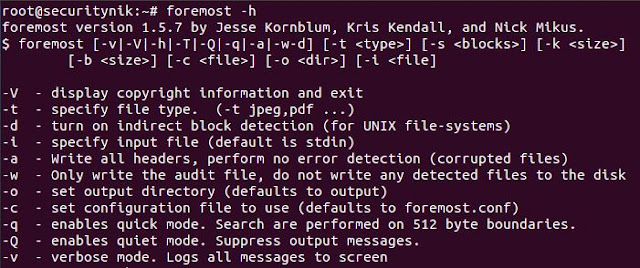
Before running any tool you may want to see what the help has to offer in terms of guidance.
For foremost, we can execute "foremost -h" to get help as shown below.
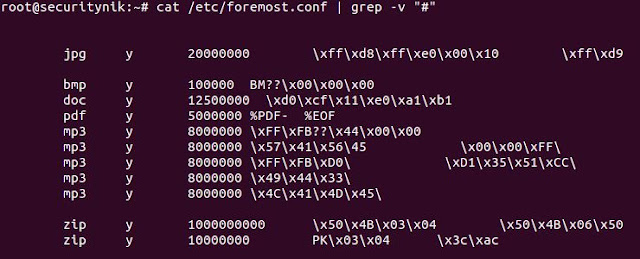
Next let's edit the foremost config file. "vi /etc/foremost.conf". I edited the default configuration file, allowing it to search for the file extensions which are on the drive. If the drive only had .pdf files I could have searched for just that. In this case I'm searching for pdf, bmp, doc, mp3 and zip. The objective was to not look for things which were not there. Additionally, it is important to understand how the "foremost.conf" file is structured as you may wish to add your own file structure to search for.
Next I create a temporary folder named "securitynikTmp" using "mkdir securitynikTmp"
Let's now run foremost to see what we get
root@securitynik:~# foremost -c /etc/foremost.conf -o securitynikTmp -v flash64.raw

- c: Tells foremost to use the configuration file which is found in "/etc/foremost.conf"
- o: Tells foremost to use output directory "securitynikTmp"
- v: Tells foremost to be verbose
flash64.raw is the file which will be used as input to foremost
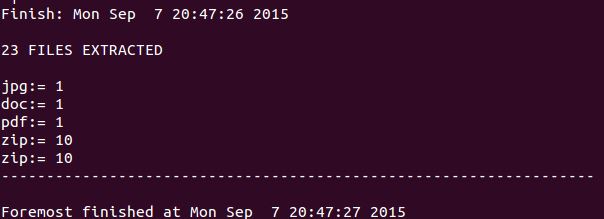
Once foremost has completed we see the following (note that the actual files extracted has been omitted for brevity).
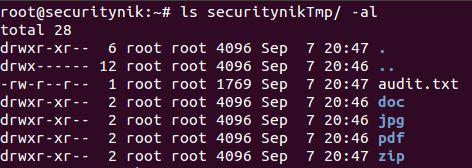
Next if we perform a "ls" on the "securitynikTmp" folder, we see the following listing showing that foremost created a folder for each file extension type.
The "audit.txt" shows the output from the execution of the foremost command. Basically this information is much similar (if not the same) to the information which was seen on the screen during the execution of foremost.
Let's now look at the "pdf" folders. Below we see there was one pdf file.

Let's open this file using "xpdf" and see what the contents provide us.
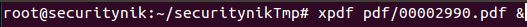
As we can see the pdf file opened successfully.
That's it for foremost. Next post we will use scalpel to perform the similar task.
References:
Foremost
xpdf
dcfldd

Next we verify that both the output file and the log files are created and below we see they are.
 Now let's use foremost to see if we can retrieve the same data as shown above.
Now let's use foremost to see if we can retrieve the same data as shown above.Before running any tool you may want to see what the help has to offer in terms of guidance.
For foremost, we can execute "foremost -h" to get help as shown below.

Next let's edit the foremost config file. "vi /etc/foremost.conf". I edited the default configuration file, allowing it to search for the file extensions which are on the drive. If the drive only had .pdf files I could have searched for just that. In this case I'm searching for pdf, bmp, doc, mp3 and zip. The objective was to not look for things which were not there. Additionally, it is important to understand how the "foremost.conf" file is structured as you may wish to add your own file structure to search for.

Next I create a temporary folder named "securitynikTmp" using "mkdir securitynikTmp"
Let's now run foremost to see what we get
root@securitynik:~# foremost -c /etc/foremost.conf -o securitynikTmp -v flash64.raw
- c: Tells foremost to use the configuration file which is found in "/etc/foremost.conf"
- o: Tells foremost to use output directory "securitynikTmp"
- v: Tells foremost to be verbose
flash64.raw is the file which will be used as input to foremost
Once foremost has completed we see the following (note that the actual files extracted has been omitted for brevity).

Next if we perform a "ls" on the "securitynikTmp" folder, we see the following listing showing that foremost created a folder for each file extension type.

The "audit.txt" shows the output from the execution of the foremost command. Basically this information is much similar (if not the same) to the information which was seen on the screen during the execution of foremost.
Let's now look at the "pdf" folders. Below we see there was one pdf file.

Let's open this file using "xpdf" and see what the contents provide us.

As we can see the pdf file opened successfully.

That's it for foremost. Next post we will use scalpel to perform the similar task.
References:
Foremost
xpdf
dcfldd
Subscribe to:
Posts (Atom)


