As with most Linux tools, before running them you may wish to see what the options are for execution by looking at the help. In this case to get help from scalpel type "scalpel -h"
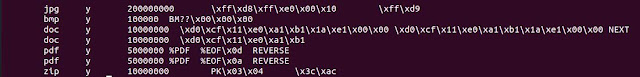
Similar to the foremost post, I also modified the "scalpel.conf" file to just focus on the files which I know are on the drives.
Let's now execute scalpel
scalpel -c /etc/scalpel/scalpel.conf -o securitynikTmp/ -v flash64.raw
- c: Tells scalpel to use the configuration file which is found in "/etc/scalpel/scalpel.conf"
- o: Tells scapel to use output directory "securitynikTmp"
- v: Tells scalpel to be verbose
flash64.raw is the file which will be used as input to scalpel
Now that scalpel has executed we perform a "ls" on the "securitynikTmp" folder and see the following:

Let's look at the audit.txt to see what was extracted
root@securitynik:~# cat securitynikTmp/audit.txt
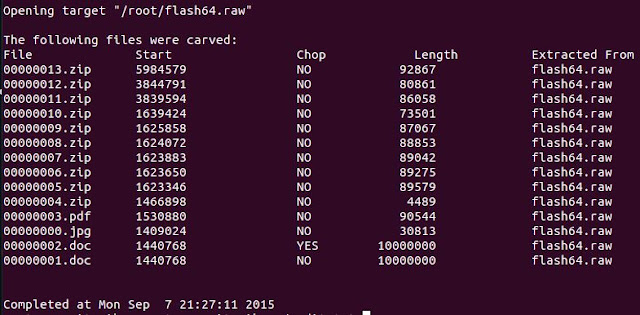
Let's look to see how well the .jpg file was extracted
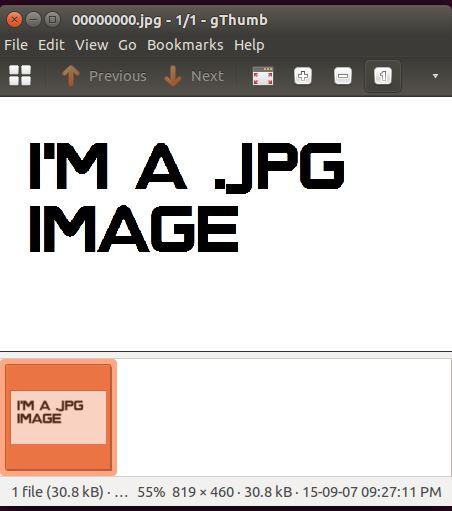
So far so good. Looks like we successfully extracted the .jpg file because we have opened and can view it with gthumb.
While tools like foremost and scalpel are helpful for automatically retrieving these files, it is also important that we understand how to do this process manually. In the next post we will leverage information learned from foremost and scalpel to manually carve a file.
References:
scalpel
gthumb


Great
ReplyDelete