The idea here is that that you learned a host in your infrastructure is running "VBoxService.exe". You would now like to know if there are other hosts within your environment that is running the same process. To figure out what is going on we can first try the following.
C:\>WMIC /Node:127.0.0.1,10.0.2.15 PROCESS WHERE Name="VBoxService.exe" GET CSName, Name, ExecutablePath, ProcessID, ParentProcessID
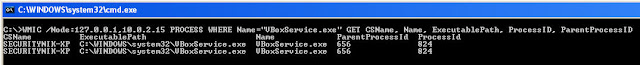
From the above, we see we were able to look across hosts 127.0.0.1 and 10.0.2.15 to identify which hosts may be running the "VBoxService.exe" process. However, the problem with this method is its not quite scalable. Imagine appending (or prepending) IPs to the list. This can become a major problem to manage.
The alternative (which is better) is to provide WMIC a list of IPs in a file and let it read the values from the file.
Let's try the previous command again. This time by providing an input file.
I've created a file named "myNodes.txt" which contains the 2 IPs we just used. Below shows the file and its contents.
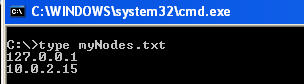
Now let's run this against WMIC.
C:\>WMIC /Node:127.0.0.1,10.0.2.15 PROCESS WHERE Name="VBoxService.exe" GET CSName, Name, ExecutablePath, ProcessID, ParentProcessID
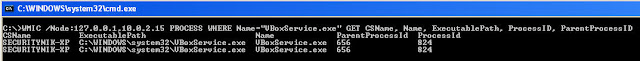
The output above shows that host "SECURITYNIK-XP" (note the 2 instances of it because basically I was targeting the same system from two different IPs) has the process running.
From the above image, we see that by adding a list of IPs to a file, we were able to determine where a particular process is running within an infrastructure.
Go ahead and try to see how you can leverage WMIC in your environment if you have not been doing so already
Well that's it for this post!
No comments:
Post a Comment