So now that you are there, the first thing you decide to do ... after taking a memory dump ... is to run WMIC to get the system name. Let's do that.
C:\>WMIC COMPUTERSYSTEM LIST BRIEF
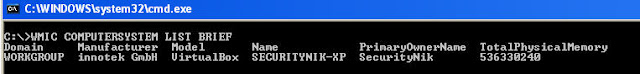
While this provided helpful information there was more we could have gotten if we had run
C:\>WMIC COMPUTERSYSTEM LIST FULL
However, the previous command would give us probably a little bit more than we need at this time. As a result, let's be picky about the information we would like.
C:\>WMIC COMPUTERSYSTEM GET Domain, Model, Name, PartOfDomain, UserName, SystemType, TotalPhysicalMemory
 From the above we see we were able to extract the Domain the computer is in, its name, whether or not it is part of a domain, the username of the currently logged in user, the system type and the total physical memory.
From the above we see we were able to extract the Domain the computer is in, its name, whether or not it is part of a domain, the username of the currently logged in user, the system type and the total physical memory.Looks like we at least know a little about the system. Hope you are documenting your steps so far :-)
Let's look to see what programs are running
C:\>WMIC PROCESS LIST BRIEF
 While the above image shows very useful information, there is still a bit that is left out.
While the above image shows very useful information, there is still a bit that is left out. If we were to use the "C:\>WMIC PROCESS LIST FULL" we would get lots of information. More than we need. Let's focus in on the information which would probably be helpful.
C:\>WMIC PROCESS GET Name, ExecutablePath, HandleCount, ProcessID, ParentProcessID
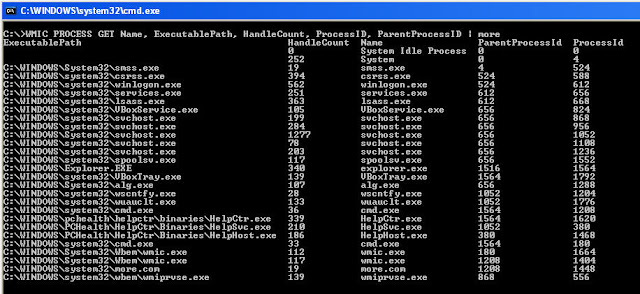
From the above we see we have a nice view which now includes the executable path of the process. We also have the handle count which shows the number of handles which the process has opened. Additionally, we see the process id and parent process id. This is much more useful information.
So now that we've identified the list of processes, let's take a specific process and gather all the information available for it.
C:\>WMIC PROCESS WHERE Processid=824 LIST FULL
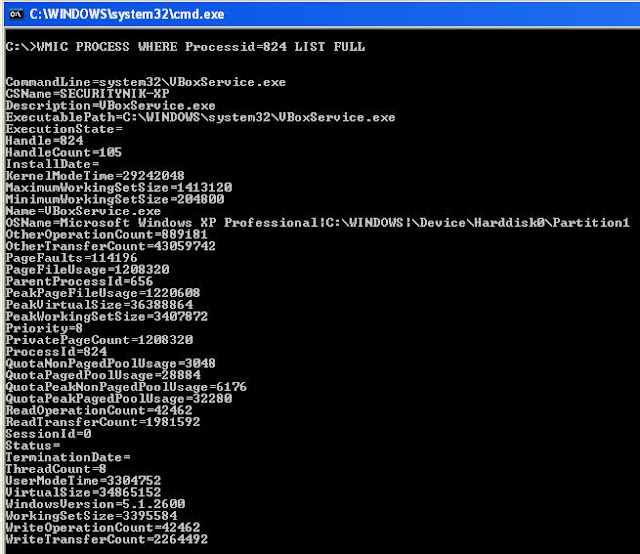
From the above we see that we've learned all the information that is available for a specific process
For the rest of the way, we will use "LIST BRIEF", "LIST FULL" AND "GET" as needed. We already know we can get some information from "list brief" and a lot from "list full". However, it is best if we target the information which may be useful to us at for this investigation.
Let's find out the users who are currently created on the system..
C:\>WMIC USERACCOUNT GET Caption, FullName, Name
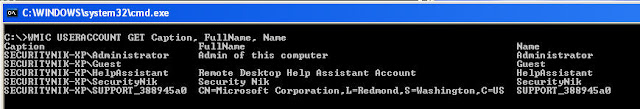
Now that we have the list of users on the system. Let's take a look at their network login information
C:\>WMIC NETLOGIN GET FullName, UserID, LastLogon, Name, UserType
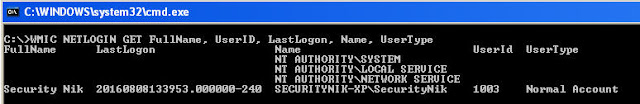
From the above we were able to grab the logged on user name, full name, last logon and user type
Ok. I will stop now. The idea was to show that you can leverage WMIC which is built into Windows to gather information which you would have typically gathered from other tools, some built into Windows while some are 3rd party.
See the next post for information on leveraging WMIC for "live" remote forensics.
No comments:
Post a Comment